Hackers in Order to Install Frebniis Malware Hacks IIS Feature

“Frebniis, the malware uses a method that injects harmful code into iisfreb.dll’s memory. Iisfreb.dll is a DLL file attached with an IIS feature used for checking unsuccessful web page requests.”
“Frebniss” is a new sort of malware that recently posed a threat to Microsoft’s Internet Information Services (IIS).
Also Read, What is the ‘North Korean Hacking’ fiasco in the cryptocurrency fiasco?
The malware is being employed by hackers to help them carry out stealthy commands using web requests that are transmitted through the internet.
Microsoft IIS is a robust software app platform uses for web application hosting and web server functionality. Among its multiple uses, the software application platform serves crucial services of Microsoft such as Outlook.
Microsoft IIS is a trusted platform and enables users to get easy access to services and web applications, making it a preferred choice for businesses and individuals simultaneously.
Frebniis Corrupts IIS Feature
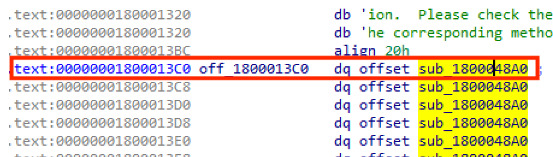
Frebniis, the malware uses a method that injects harmful code into iisfreb.dll’s memory. Iisfreb.dll is a DLL file attached with an IIS feature uses for checking unsuccessful web page requests.
With the help of the IIS feature, all HTTP requests are stealthily tracked by Frebniis and detect particular formats of requests from the hacker, leading to the possibility of executing remote code.
The hacker must get access to the Windows system operating the IIS server utilizing another method to apply this trick. But, how the hacker got this access in this instance remains uncertain.
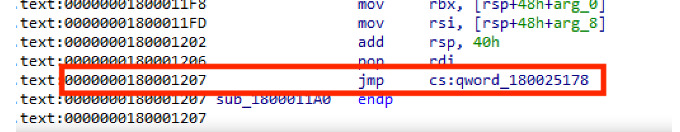
The injected .NET backdoor allows C# code execution and helps in proxying without doing disk interaction which makes it undetectable. A particular password is checked when default[.]aspx or logon[.]aspx are requested.
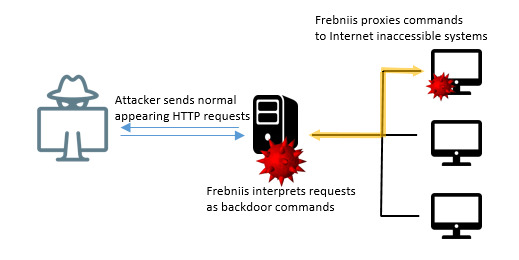
Frebniis can command and link with other systems via compromised IIS, utilizing a base64 encoded string as a second HTTP parameter, accessing secured internal systems which are publicly unavailable.
