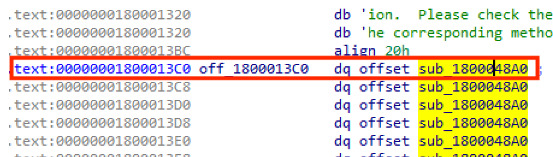
“According to the latest event, researchers have discovered that certain cyber attacks can exploit the latest version of WordPress. Authorities have asked users of the Advanced Custom Fields plugin for WordPress to update. They urged to make the update to version 6.1.6 of WordPress.”
WordPress, a widely used CMS is a free and open-source CMS written in hypertext preprocessor language and coupled with a MySQL or MariaDB database. WordPress, which powers 43% of the web, updates itself yearly as a content management system (CMS).
Also Read, Halcyon Gets $50M Fund for Anti-Ransomware Tool Development
According to the latest event, researchers have discovered that certain cyber attacks can exploit the latest version of WordPress. Authorities have asked users of the Advanced Custom Fields plugin for WordPress to update. They urged to make the update to version 6.1.6 of WordPress.
The vulnerability, known as CVE-2023-30777, represents a case of reflected cross-site scripting (XSS). Malicious actors can exploit this vulnerability to inject absurd executable scripts into otherwise benign websites.
Users have installed the Advanced Custom Fields plugin, available in both pro and free versions, more than two million times. Security researchers discovered and reported the vulnerability to the WordPress team on May 2, 2023.
Patchstack researcher Rafie Muhammad said, “This vulnerability allows any unauthenticated user to steal sensitive information. In this case, the vulnerability enables privilege escalation on the WordPress site by tricking a privileged user into visiting the crafted URL path.”
Users can experience reflected XSS cyber attacks when they unknowingly click on a fake link sent through email or other means, such as messages. This action allows malicious code to infiltrate the vulnerable website, which then reflects the attack back to the user’s browser.
Imperva, a cyber security leader notes, “[A reflected XSS attack] is typically a result of incoming requests not being sufficiently sanitized, which allows for the manipulation of a web application’s functions and the activation of malicious scripts,”
It is worth noting that the vulnerability CVE-2023-30777 can start on the configuration of Advanced Custom Fields or on a default installation. However, only logged-in accounts with plugin access can perform this task.