“Known as the ‘Untitled Goose Tool’ and developed along with Sandia, a U.S. Department of Energy national laboratory, the tool can dump telemetry information from Microsoft 365, Microsoft Azure, and Azure Active Directory.”
CISA, the American Cybersecurity & Infrastructure Security Agency has released a new open-source incident response (OSIR) tool designed to detect signs of unauthorized activity in Microsoft cloud environments.
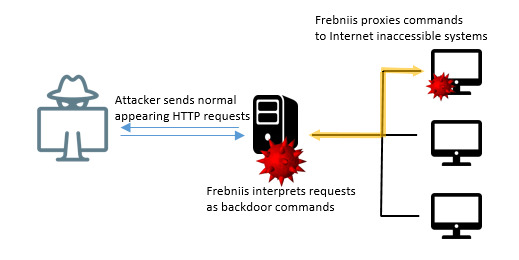
Also Read, Hackers in Order to Install Frebniis Malware Hacks IIS Feature
Known as the ‘Untitled Goose Tool’ and developed along with Sandia, a U.S. Department of Energy national laboratory, the tool can dump telemetry information from Microsoft 365, Microsoft Azure, and Azure Active Directory.
CISA said, “Untitled Goose Tool is a robust and flexible hunt and incident response tool that adds novel authentication and data gathering methods in order to run a full investigation against a customer’s Azure Active Directory (AzureAD), Azure, and M365 environments. Untitled Goose Tool gathers additional telemetry from Microsoft Defender for Endpoint (MDE) and Defender for Internet of Things (IoT) (D4IoT).”
With the help of Microsoft cloud interrogation and analysis tool of CISA, security networks, and experts will be able to –
- Export and review Microsoft Defender for IoT alerts, Azure activity logs, M365 unified audit log, AAD sign-in and audit logs, and Microsoft Defender for Endpoint data for suspicious activity.
- Query, export, and investigate Azure, AAD, and M365 configurations.
- Draw out cloud artifacts from Microsoft’s M365, AAD, and Azure environments without executing additional analytics.
- Managing time bounding of the UAL.
Earlier in March 2023, an open-source tool called ‘Decider’ was released by CISA to help defenders generate MITRE ATT&CK mapping reports to fine-tune their security posture based on the tactics and techniques of adversaries.
Decider was launched when a “best practices” guide about MITRE ATT&CK mapping in January was published, highlighting the imperativeness of using the standard. It also announced that starting January 2023, it would alert critical infrastructure entities of Internet-based systems susceptible to ransomware attacks.